Security Configuration and Analysis tool: Step by Step
Maintaining consistency in security/audit/group policy settings have been a manual task in large and diversified organizations where servers are scattered across LAN and DMZ segment of the network. Domain Joined machines actually get their common settings propagated and applied from Group Policy objects defined at the domain level but when it comes to DMZ machines which are not part of Domain it becomes a real challenge to define those settings manually and make them consistent in terms of server hardening or group policy settings.
Please note that 'not' all the settings available in Group policy can be configured using this method but for server hardening purpose, minimum security settings can be applied which contains Audit and security policies. (Everything available in Local Security Policy Snap-In)
Lets review and try our hands on a tool which has not been talked much about the Windows System administration arena.
We have a Target machine which has been fresh built with Windows 2008 R2:
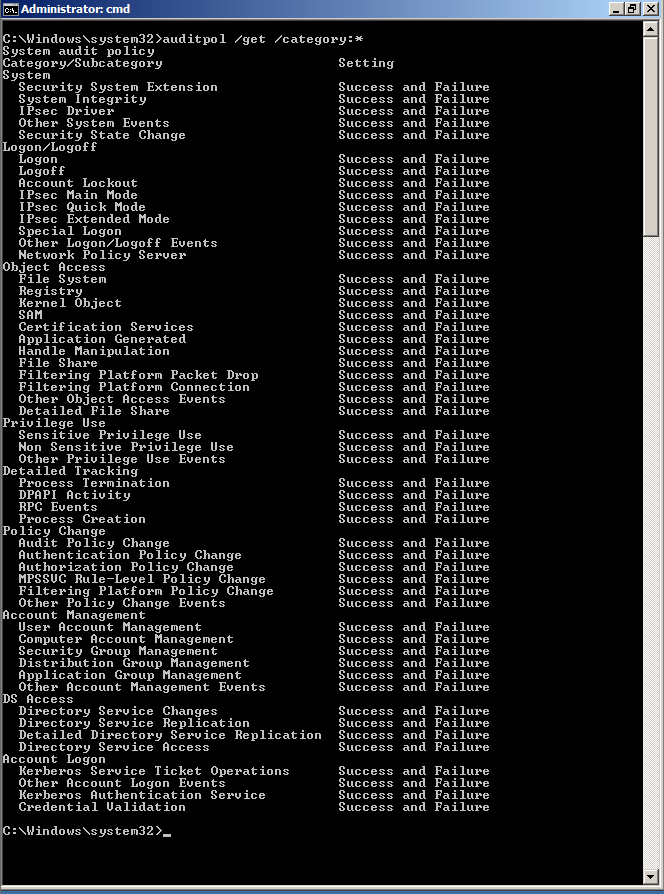
Open Command Prompt type below command to see what policies are there by Default:
Auditpol /get /category:*
As we can see above, the policies defined are very minimal:
Now we will create a security database along with custom defined configuration file to apply the settings to other target machines.
Open Secpol.msc aka Local Security Policy
Start > RUN > Secpol.msc
We see that the policies are not defined at the moment.
Lets define them on this machine and then we will generate the configuration file along with security database.
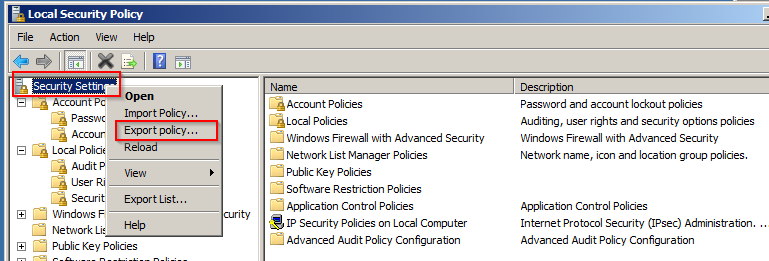
We see above that settings have been defined in the tool now lets right click on the Root (Security Settings) and select Export Policy:
Specify a location (ex: C:\Security) and give it a name (ex: Custom.Inf), The INF file generated in the above step contains all the security settings we defined here in the previous step.
(Please note that almost all of the configuration items available in this Local Security Policy snap in is configurable and after configuring them we can generate INF file which will contain all the sttings we have defined)
Now we have a security Information file and we need to generate a Security Database file (.SDB) which will be used to configure target machines with the settings defined in the database and Config File.
Open MMC > File > Add Remove Snap-in (Ctrl +M) > Select Security Configuration and Analysis from the available snap-ins pane > click Add > and click OK
It will add the Security Configuration and Analysis snap-in to the mmc console under Console Root
Expand Security Configuration and Analysis (click on +) > right click > select Open Database:
We don't have an SDB file yet so select the location where inf file was saved in the last step and give any name and it will create a blank SDB file and after that it will ask for the Configuration file > select the INF file located there and click Open:
Now we have SDB database file created which contains all the settings which were defined in the Configuration file.
So we have a set of two files now :
Custom.inf
Custom.sdb
Now lets go to a new machine assuming it as one of the target DMZ Machine which does not any custom policy defined yet.
Lets check the security policy settings defined on this now:
Open Command Prompt type below command to see what policies are there by Default:
Auditpol /get /category:*
It shows same as the previous server which we started with having minimal settings defined:
Now We will configure this server using the SDB and INF file we created on the previous server.
Open MMC > Security Configuration and Analysis snap-in > Right Click > Select Open Database > Select the Custom.SDB file we generated in one of the previous steps:
After opening the SDB file > Right Click on Security Configuration and Analysis and Select
"Analyze Computer Now"
It will ask for a Log file location, specify one and hit OK. After the progress bar disappears lets review the settings defined on system vs the settings available in the SDB file.
Notice here that the settings in right hand pane shows two columns:
Database Settings: Contains setting defined in the SDB file.
Computer Setting : Actual Setting on the computer now.
Each setting has a red cross or green check mark on it which tells if that particular setting defined on computer is complaint with that in the SDB file or not.
We can simply right click Security Configuration and Analysis again and and click Configure Computer Now... which configure the target computer with all the settings defined in the SDB File:
For example: We have defined several other settings along with a setting to rename Administrator and Guest accounts to Administrator_Renamed and Guest_Renamed.
Lets check the account status now and then after performing configuration we will check if the accounts were renamed or not.
Now lets configure the Server:
Right Click Security Configuration and Analysis Select Configure Computer Now... hit OK when prompted for the log file path.
A progress will appear and will finish.
Lets check the status of Administrator and Guest Accounts now.
If it does not reflect you might need to do Gpupdate /force and check the status of accounts again.
Open the Database file (.SDB) file again and perform another analysis to see of the settings have been applied and all items are showing with Green Check Mark Now
The above results shows that the settings have been applied successfully and settings defined in database as well as Server are all identical and have green check marks:
Lets do a final policy check on the command prompt:
Review the screenshot above it shows everything defined with success and failure (Whatever we specified).
Go ahead and check in Gpedit.msc (Start > Run > gpedit.msc) and double check if all the settings we have specified have been set or not. (If they don't reflect do gpupdate /force)
Bonus Tip:
Performing Security Analysis and configuration using GUI can be a cumbersome task when we need to automate or script it to run on multiple systems so for that we have a Command line utility which accepts .SDB file and .INF File and allows us to perform analysis as well as configuration of target machines.
Analyze:
secedit /analyze /db Custom.sdb /cfg Custom.inf /log analyze.log
It will generate a Log file called analyze.log at the above mentioned location which location whic will tell you what configuration settings are defined and what is the analysis result.
Now to configure all the settings defined in .SDB and .INF file we can supply below command:
Configure:
secedit /configure /db Custom.sdb /cfg Custom.inf /overwrite /log Configure.log /quiet
It will prompt you whether you want to overwrite all the settings defined on local machine with those available in the .SDB file.
Type in "Y" to proceed with configuration.
Good Luck!!!













I repaired many computer in past by it which performance is very good in computer networking business. IT Support Broward
ReplyDeleteWow nice computers hardware service in chap price by computer service in USA.
ReplyDeleteData Recovery Boca Raton
This is a really good read for me, Must admit that you are one of the best bloggers I ever saw.Thanks for posting this informative article. I really like the fresh perceptive you did on the issue. I will be back soon to check up on new posts! Thank you!
ReplyDeleteBest gaming computer
I am glad you liked it :)
Delete